Certificates in SAP Systems
In this digital era, data is the most valuable asset, even more than gold. Hence Security is top most priority for any system in IT. And SAP is no exception to this. Now days everything is access via Web or Internet. Hence its must to have all security measures implemented while accessing systems on internet. This is achieved by the installing Certificates on the Web Server.
An organization needs to install the SSL Certificate onto its web server to initiate a secure session with browsers. Once a secure connection is established, all web traffic between the web server and the web browser will be secure.
What are Certificates
Certificates or SSL (Secure Socket Layer) Certificates are small data files that digitally bind a cryptographic key to an organization’s details. When installed on a web server, it activates the padlock and the https protocol and allows secure connections from a web server to a browser.
SSL Certificates bind together :
- A domain name, server name or hostname.
- An organizational identity (i.e. company name) and location.
Cryptography is way or science of sending secret messages. When it comes to SSL, SAP uses Public Key Cryptography, which is based on PKI (Public Key Infrastructure). This particular kind of cryptography harnesses the power of two keys which are long strings of randomly generated numbers. One is called a private key and one is called a public key. A public key is known to your server and available in the public domain. It can be used to encrypt message.
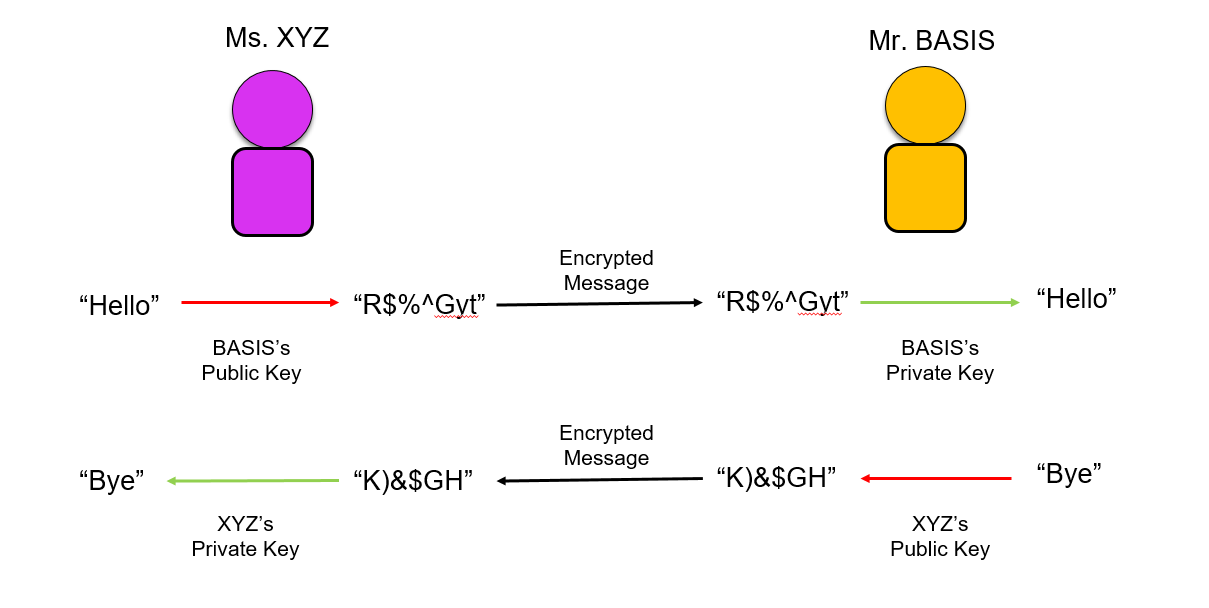
How Public and Private Key Works
Lets take a scenario, Ms. XYZ and Mr. BASIS are two good friends. XYZ want to send a secret message to BASIS so that no one can see it. Hence she uses Public Key from BASIS to encrypt it. Now as message is encrypted, no one can read it, except BASIS as he has the Private Key to decrypt the message. So simple right.
Certificate Details
While working with certificates, we often hear terms like CA, PKI, TLS, DN, CN and so on. Lets check what is actually mean by these.
- CA (Certificate Authority) – Responsible for Root/Intermediate Cert
- PKI (Public Key Infrastructure) – It’s Platform
- TLS – Transport Layer Security Protocol, Current Versions are TLS 1.0, 1.1, 1.2. For details please refer SAP Note 2781565 & 510007.
- DN – Distinguished Name
- CN – Common Name
- SSL – Secured Socket Layer
- PSE – Personal Security Enviroment
CA or Certificate Authority is the one who issue or sign the Certificates created, thus binding those with the CA’s Root Certificate and Intermediate Certificate. On very broad scale you can consider Root certificate as CA’s Private key as per example we discussed previously.
When ever certificates are created, those will be by default Self Signed means not signed by external CA. Thus security level of such Self Signed Certificates is very low and hence not recommended. Creation of Certificate in SAP means creation of DN which consist of below details
- DN (Distinguished Name)
- CN (Common Name)
- OU (Organization Unit)
- O (Organization)
- S (State)
- L (Locality)
- C (Country)
- SAN (Subject Alternative Name)
As name suggest, each entity defines the organization and combining all creates a unique DN. Once its created, we need to create a CSR request which is encoded form of the cert which will be then Signed by the CA. When CA signed the cert, they provide their own root and intermediate cert. Thus while importing the signed response from CA in our certificate, we need to make sure that we import root and intermediate cert as well, completing the certificate chain.
How to access Certificates
In SAP R/3 or ABAP system, you can access it via transaction STRUSTSSO2. This transaction mainly deals with PSE which consist of DN. Types of PSEs are as follows.
- System PSE
- SSL Server PSE
- SSL Client PSE
- SNC PSE
- Anonymous PSE
While working with SSO (Single Sign-On) via SSL, we mainly interact with SSL Server PSE and SSL Client PSE by exchanging certificates between two SAP Systems. In case of any issue, you can troubleshoot it by checking logs in transaction SMICM.
In case of JAVA systems, you can access certificates via Visual Admin or NWA. Now a days with latest version of SAP NW, Visual Admin is void and only NWA is available as admin access tool. In JAVA, certificates mainly available via Key Store which consist of different Views like Default, TicketKeyStore, TrustedCAs etc. But main part of any view is Key-Pair Cert which is nothing but a DN which we discussed previously.
For rest of the SAP systems like Web Dispatcher or HANA, certificates are accessible via respective PSE management tools (Admin URLs) or via Key Stores. HANA system internally used Web Dispatcher only, thus accessing PSEs is same i.e. via admin URL.
Certificate Checks
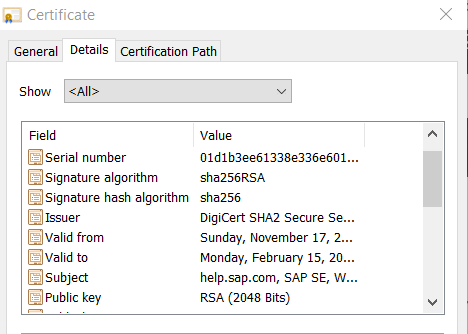
You can check certificates if those are active and accepted by browser by looking for the Padlock.
If you double click on it, it will show details for the certificate.
Very simple right. So next time you visit any website do verify the padlock and certificate validity. Also make sure that your SAP system Web host have Signed Certificate installed and accessible with padlock.